Security assessments are a detailed and comprehensive analysis of the security situation of a company or organization with mandatory recommendations and instructions for controlling and eliminating assessed risks. The security assessment includes a security study that identifies hazards and sources of threat with a risk treatment plan to implemented by internal services and sectors, but also partner companies that provide physical and technical protection, information security and security of persons, property, and business in the broadest sense.
The process of preparation of studies and safety studies includes primary recording of the situation, then identification and mapping of risks, their systematization and classification, and finally defining a set of measures and activities to eliminate or reduce the identified hazards.
Our expert team will approach the preparation of the security study using modern tools, methodology and examples of best practice, which defines a new concept of security system that should come to life in the organization and accepted by management.
We efficiently and comprehensively observe and assess the current situation through independent and professional expertise, provide suggestions, instructions and solutions for all recorded weaknesses and vulnerabilities that may be the cause of serious business losses.
The basic elements of our checks that included in the security study are:
- Quality, professionalism, level of training and readiness of personnel engaged in the field of physical security, as well as their professional integrity, reliability, and attitude towards work.
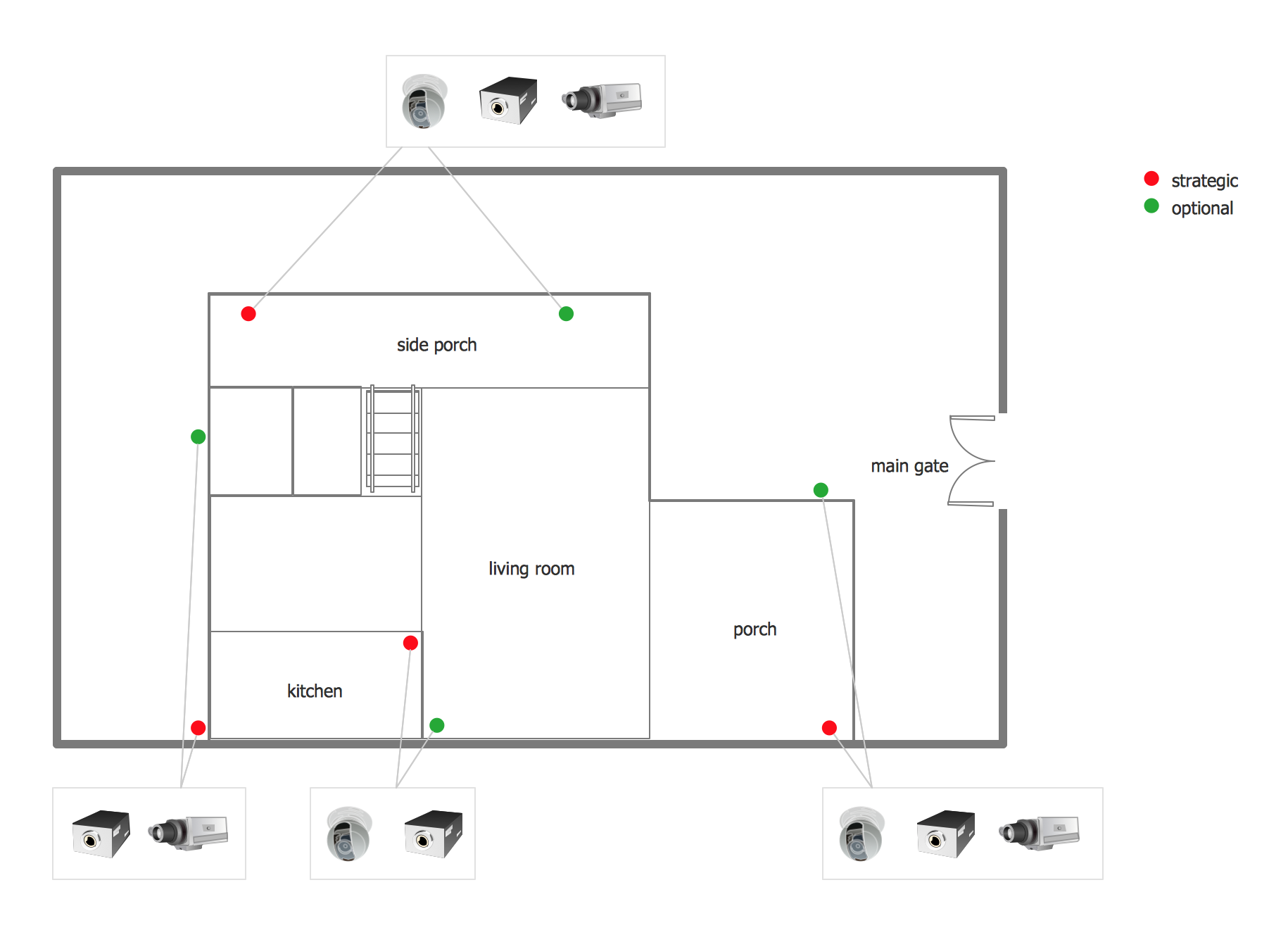
- Compatibility, economy, efficiency, and up-to-datedness of the system of technical protection of facilities, property, and business (Video surveillance – CCTV, Alarm monitoring, fire alarm, access control, security locks and doors, other mechanical and electronic protection).
- Improvements and proposals for the integration of technical systems to achieve the possibility that the same resources used to monitor business processes.
- Audit of the condition of the fire protection system and safety and health protection at work with verification of compliance with legal regulations.
- Evaluation and verification of the security culture of employees, managers, senior and middle management as well as defining an action plan for raising corporate security through the education program.
Every system should have a security study created and be ready to constantly improve and review the security study, because that is the only way for management to manage corporate security successfully and transparently, which is an indispensable item of sustainability and development.
The organization’s security plan is prepared to implement the measures from the Act on Risk Assessment in the Protection of Persons, Property and Business, and this document, depending on the risk assessment or the requirements of the organizations themselves, contains the necessary planning measures, activities and procedures:
- preventing unauthorized access to the facility.
- signals of unauthorized entry into the protected area and notification to the control center.
- preventing the introduction of weapons, explosives, radioactive, biological, and other dangerous objects, and substances into the facility.
- protection of individual values by means of electrochemical systems and other methods of protection (suitcases, containers, cash registers, safes, etch).
- performing actions aimed at preventing criminal acts.
- monitoring movements in and around the protected area, as well as in individually protected areas.
- controls on the implementation of prescribed protection measures and internal order in the facility and parts under a special regime.
- integrated protection with or without local supervision and with a system of communication with security officers at the protected facility.
- undertaking procedures in order of priority for cases of risk occurrence.
The development of a security plan can follow only after the preparation of the risk assessment, its detailed analysis, especially in terms of the proposed treatment and treatment of risk, then, the assessment and analysis of its own capabilities, potentials, and capacities. When all the preparatory activities completed, the company’s management, at the suggestion of the security manager, decides on the development of a security plan.
The security plan represents the final phase of the process of planning the security and protection system of the corporation, so it can say that it is a concretization of all previous planning activities. The security plan contains the response of the business organization in case of crises, emergencies, and specific security incidents. The company’s security plan, by its nature, is an operational document which contains and elaborates all activities related to risk assessment, treatment of identified hazards, analysis of exposure of individual sectors, assessment of own potentials and available resources in terms of preparing responses in case of any threat. types, and the identification and definition of specific mechanisms, procedures and operational measures and activities undertaken by entities within the company, to prevent and eliminate hazards, including remediation and recovery measures.